
Ransomware in Healthcare: How Backup, Detection, and Resilience Can Keep the Lights On
The recent cyberattack on the Community Clinic of Maui is another reminder of how ransomware continues to target the healthcare industry.
The real impact hit when the clinic had to shut down for nearly two weeks
Taking a look at this attack highights the real-world impact it has, the clinic was forced to close for nearly two weeks. Over 123,000 people’s sensitive information stolen—including Social Security numbers and even medical treatment details. Staff resorted to paper charts, and patients lost access to care, showing just how disruptive these attacks can be beyond the data breach itself.
What’s really needed in situations like this? It starts with a comprehensive approach to security—one that goes beyond just keeping hackers out. Yes, having solid firewalls and security systems in place is critical, but healthcare providers also need early breach detection tools to catch these threats before they spiral out of control. An example of this is the newly announced Veeam Recon Scanner.
Recon Scanner proactively spots unusual network activity, suspicious file behaviour, data exfiltration attempts, and even brute force attacks made on the backup server - we know that most ransomware attacks target backups first. Since dwell time—the gap between compromise and attack—can be unpredictable, traditional detection struggles to keep up. By integrating proactive threat assessments into the Veeam Data Platform, customers can catch threats early, strengthening data resilience before damage is done.
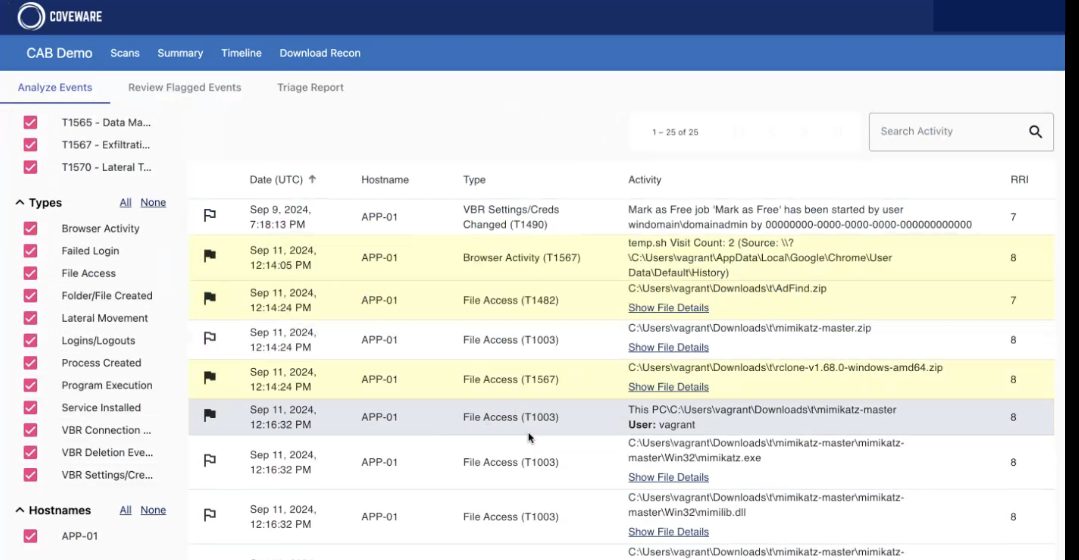
Even with the best defenses, breaches can happen, so post-breach analysis is a must. This allows organisations to dig into what went wrong, how attackers got in, and what needs to be done to prevent it from happening again. In Mālama’s case, having a robust post-breach analysis could helped pinpoint weaknesses faster and guide the response to limit downtime and data loss.
On top of backup immutability, which at this point is an absolute non-negotiable since we know attackers go after backups first - your backup server should be playing a part in early detection across your estate. Veeam Backup & Replication can provide inline scanning capabilities where entropy analysis of data streams during backups and can catch malware activities, like encrypted files (if they exceed sensitivity limits), V3 onion addresses, and ransom notes from Medusa and Clop. This can be extended further by leveraging your own YARA rules and proactively scan backup contents.
Wrapping up
So, what can healthcare organisations (or any other organisation for that matter) take away from all this? It’s about being proactive. Strengthen your cybersecurity with detection and post-breach tools, invest in immutable backups, and make sure your BCP/DR plans are airtight. In a world where ransomware is a daily threat, these layers of protection are the best shot at staying secure and avoiding the chaos that comes when systems go down.
