In case you missed it - the first part of the series. I performed object detection across a bunch of image files - check it out.
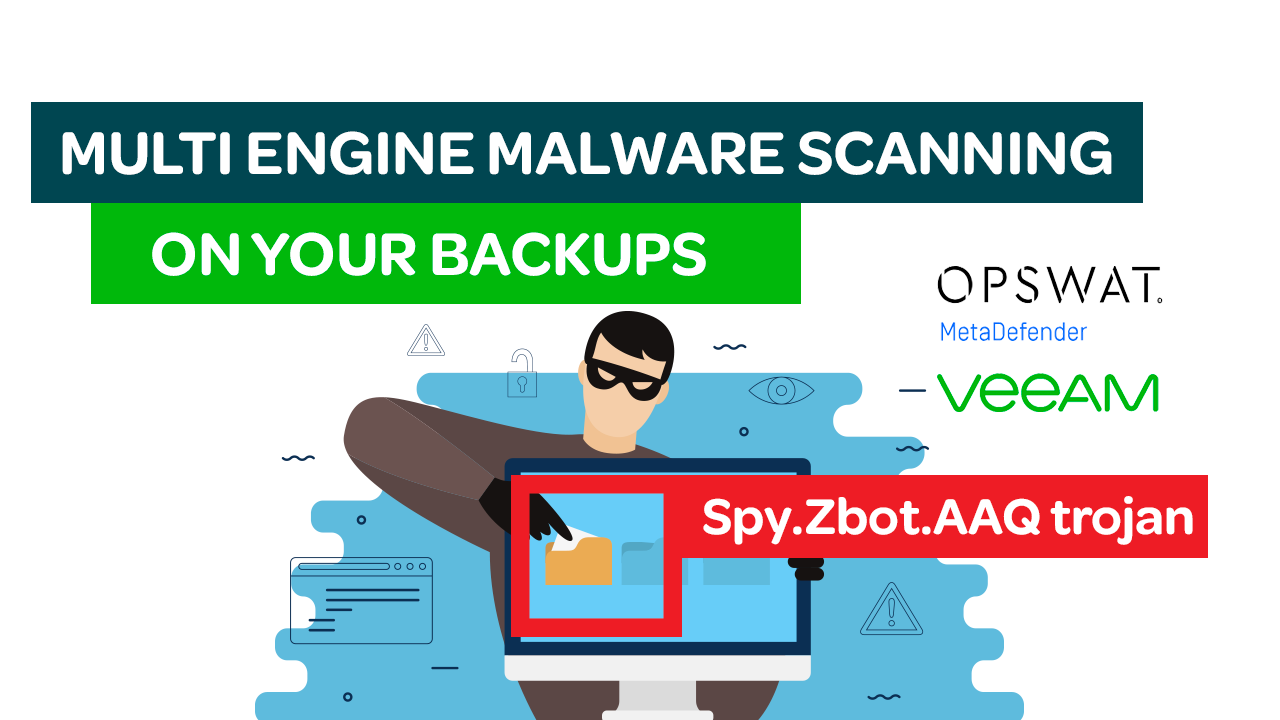
Now. Onto another use case. Have you ever wanted to run your backup data through multiple Malware/AV engines? Or retrospectively run this on all backup restore points from the last year? Running this in production would simply not be practicable from both an implementation or performance perspective. MetaDefender Cloud and the Veeam Data Integration API make this easy.
They offer a super easy to use bunch of web services that offer anything from full file upload/file scanning using through to hash databases lookups and anything in between. In the interest of making this a timely demo I am utilising the hash lookup but it would be very easy to pass up files for on demand scanning.
Demo
Pass file hashes to MetaDefender Cloud and return the result
There are notes below the video detailing a bit of what is going on here.
Notes:
- Uses the Veeam Data Integration API to mount a backup, loop through each of the objects (virtual machines) in the job, grabs the latest restore point and presents the data to a "processing" machine
- The Processing machine grabs the files and passes hashes to MetaDefender Cloud service
- Result is returned and persisted to disk for the demo so you can see what engines detected and other metadata. If Malware is found it pauses and shows the malware family/name on screen but more realistically it would be logged to a database and even warnings / logs sent to Slack, MS Teams, Ticketing systems etc
If you have Veeam Backup & Replication and want to do some things with your data - I have a starter script on a previous post to get you going.